This Azure DevOps pipelines article will show how we automate access to Microsoft Graph API using Azure DevOps pipelines.
Azure pipelines is an Azure DevOps service that allows us to automate the deployment of applications, services and changes to cloud environments.
Microsoft Graph API is the underlining API service that allows us to interact programmatically with every Microsoft 365, Intune, Entra ID, and Power Automate service using C#, JavaScript, Python, PHP, Java, Go, Azure CLI, and PowerShell.
To connect the two services, we need to create a service connection inside an Azure DevOps project. The service connection will use a managed identity. An Azure-managed identity is like a service principal without the need to manage and rotate secrets and certificates.
Create a Service Connection
To create a service connection, Open an Azure DevOps project, click on Settings, and select Service Connections from the list. Then, click Create Service connection.
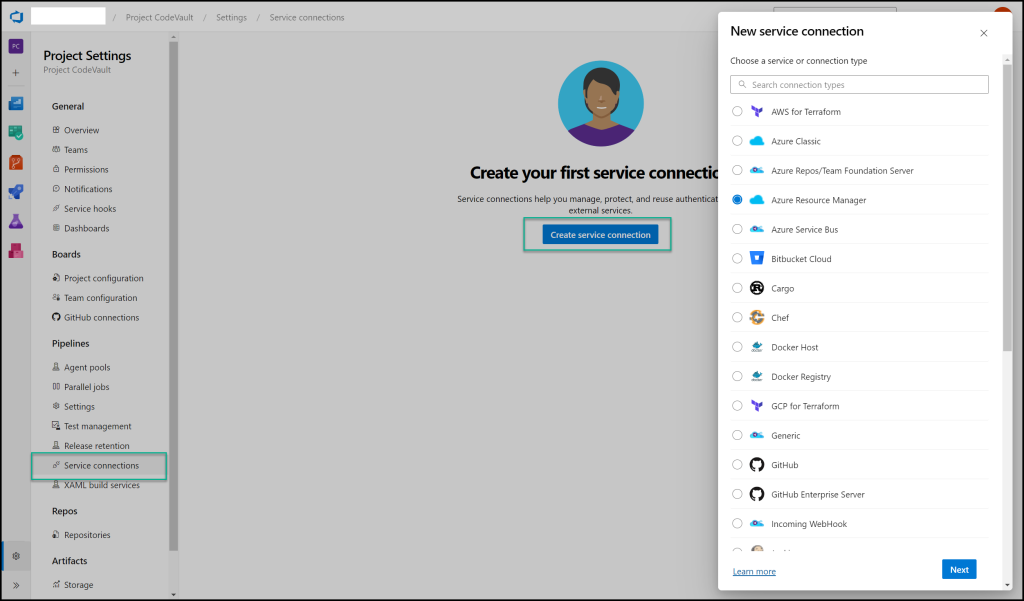
From the list of connections, select Azure Resource Manager and Workload Identity Federation (automatic)
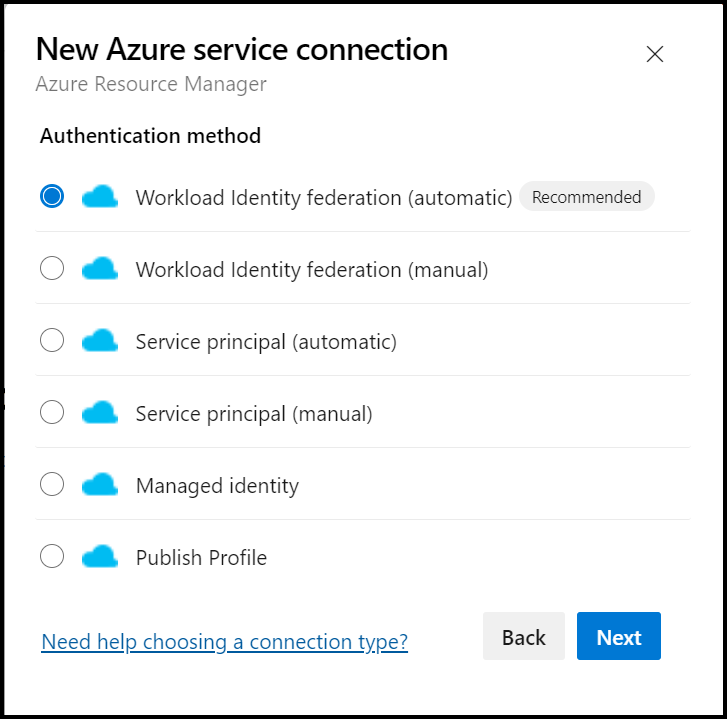
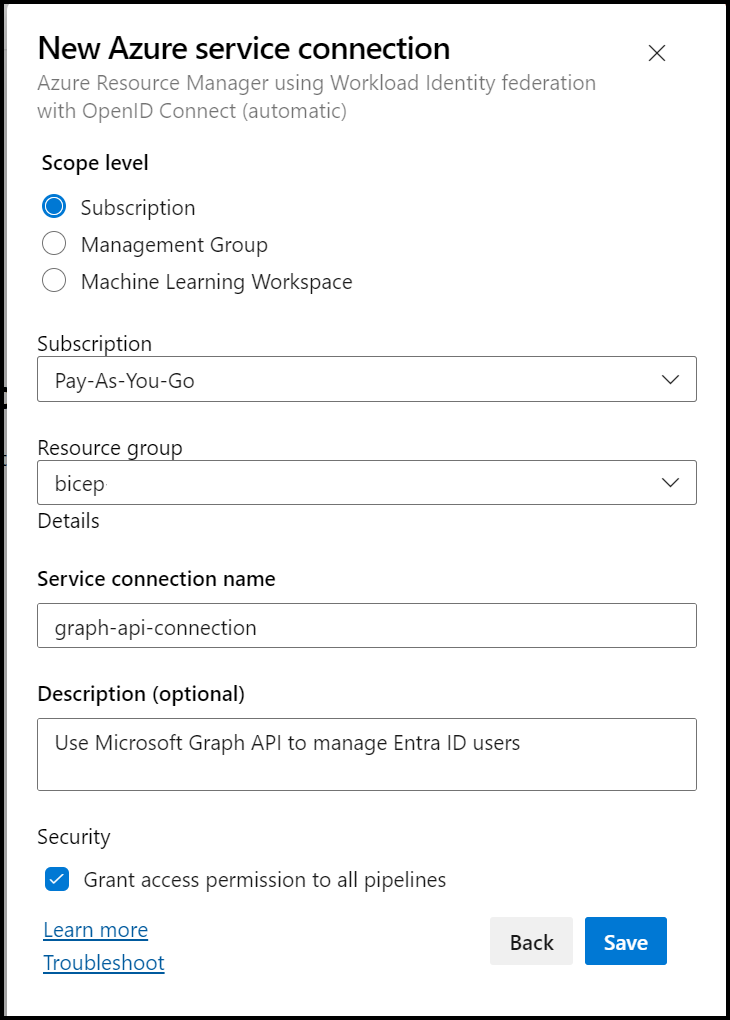
From the connection configuration page, select your Azure subscription details, Resource Group, and name, then save the connection.
Next, we need to assign the Managed-Identity account API permissions.
Grant Graph API permissions
To grant the newly created Managed-Identity account access to manage resources in Entra or other Microsoft 365 services. we need to grant it API permissions.
Open the Entra console and search for the newly created Managed-Itentiy. the name will include the Azure DevOps organisation name, project name and object ID.
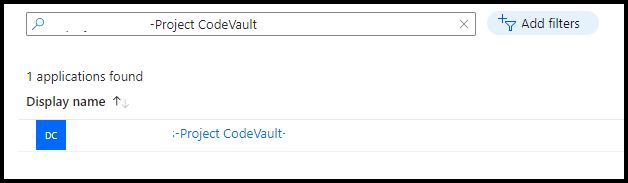
After you locate the new identity, click on it and select API Permissions
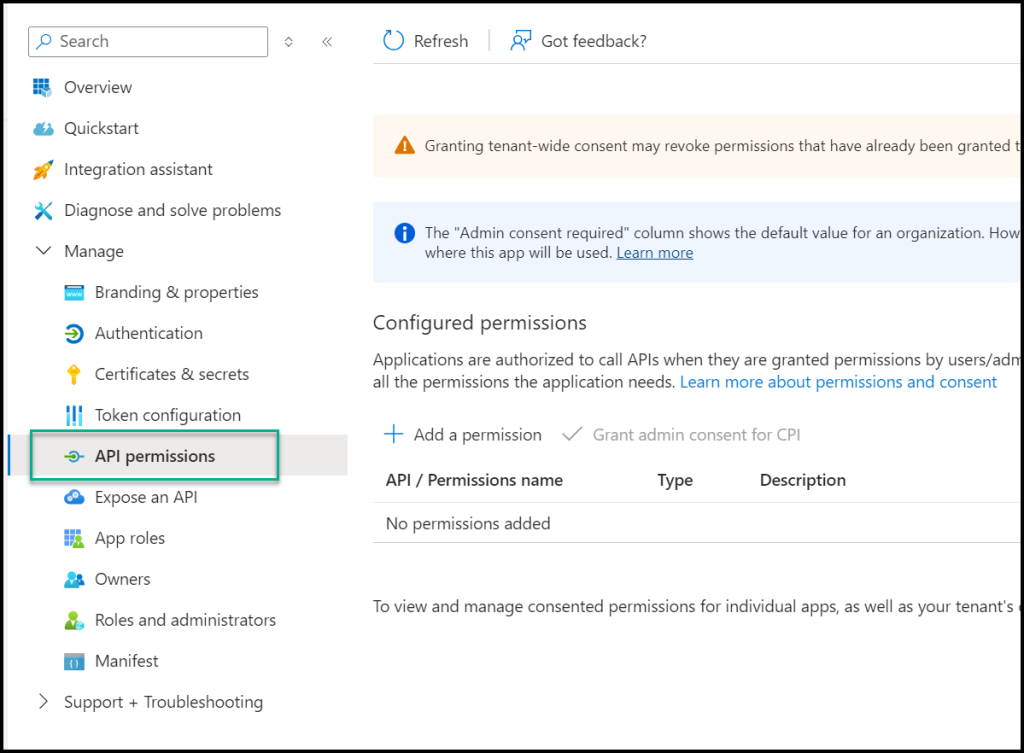
Click on Add a permission and add all the Application permissions that are needed.
Note: Make sure you use Application and not Delegated permissions.
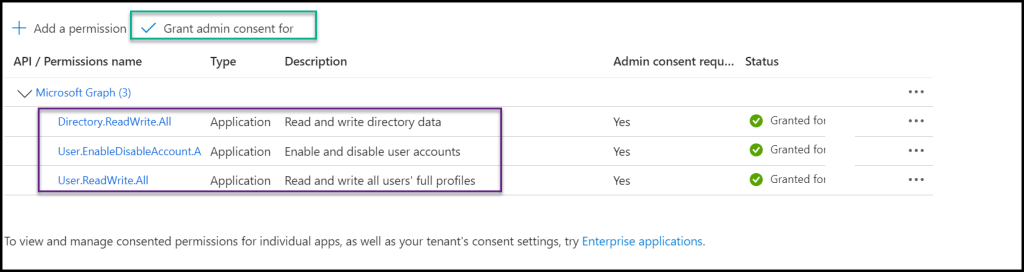
After completing this step, we can move to the final step and connect to Graph API from an Azure pipeline.
Automating Access to Microsoft Graph API Using Azure Pipelines
The final step will be connecting and using Graph API from an Azure Pipeline. In the following example, I use Azure PowerShell to request an access token and the Graph API Powershell module to run Graph API calls.
trigger:
- none
pool:
vmImage: ubuntu-latest
steps:
- task: AzurePowerShell@5
displayName: 'Get Entra access token using Azure PowerShell'
inputs:
azureSubscription: 'YOUR-SERVICE-CONNECTION-NAME'
azurePowerShellVersion: LatestVersion
ScriptType: 'InlineScript'
inline: |
$token = Get-AzAccessToken -ResourceUrl "https://graph.microsoft.com"
$accessToken = $token.Token
Write-Host "##vso[task.setvariable variable=secretToken;issecret=true]$accessToken"
- task: PowerShell@2
displayName: 'Connect to Graph API using the token from the above task'
inputs:
targetType: 'inline'
script: |
# Connect to Graph API and get Entra ID user info
$secureToken = ConvertTo-SecureString -String $(secretToken) -AsPlainText
Install-Module Microsoft.Graph.Authentication
Install-Module Microsoft.Graph.Users
Connect-MgGraph -AccessToken $secureToken
Get-MgUser -UserId "some upn"
More articles
If your organisation needs assistance with Microsoft Graph API development and automation, contact us using the form below.
Discover more from CPI Consulting -Specialist Azure Consultancy
Subscribe to get the latest posts sent to your email.


Trackbacks/Pingbacks