In this Microsoft Intune blog post, we will explain and demonstrate how to enhance Windows 11 security by implementing Attack Surface Reduction (ASR) rules.
In today’s digital landscape, securing endpoints has become more critical than ever. With the increasing sophistication of cyber threats, organizations must adopt robust security measures to protect their systems and data. One effective way to enhance security is by leveraging Microsoft Intune’s Attack Surface Reduction (ASR) rules. These rules are designed to minimize the attack surface of your Windows 11 devices, reducing the risk of exploitation and safeguarding your infrastructure.
Understanding Attack Surface Reduction (ASR) Rules
Attack Surface Reduction rules are a set of configurations available in Microsoft Intune that help mitigate risks by blocking or restricting common attack vectors. These rules are part of Microsoft Defender for Endpoint and are specifically designed to protect against various types of threats, including malware, phishing, and exploits.
Enhance Windows 11 Security With ASR rules
ASR rules play a crucial role in strengthening your organization’s security posture. By applying these rules, you can:
- Prevent malware from executing: ASR rules can block scripts and executables that are commonly used by malware to infiltrate systems.
- Mitigate phishing attacks: ASR rules can help identify and block malicious email attachments and links, reducing the risk of phishing attempts.
- Protect against exploits: ASR rules can prevent the exploitation of vulnerabilities in software and operating systems.
Implementing ASR Rules with Microsoft Intune
Microsoft Intune provides a centralized platform to manage and deploy ASR rules across your Windows 11 devices. Here’s a step-by-step guide to implementing these rules:
Step 1: Configure Microsoft Defender for Endpoint
Before you can deploy ASR rules, ensure that Microsoft Defender for Endpoint is properly configured. This involves setting up a connection between Microsoft Defender for Endpoint and Intune, as well as enabling the necessary features.
Step 2: Create an ASR Policy
In Intune, navigate to the Endpoint security section and create a new Attack Surface Reduction policy. This policy will define the specific ASR rules you want to apply to your devices.
In the Platform section select Windows and set the Profile to Attach Surface Reduction Rules
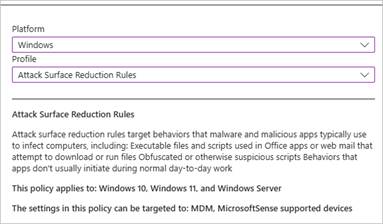
Step 3: Define ASR Rules
Select the ASR rules (see below) you want to implement from the list provided by Intune. These rules cover a wide range of security scenarios, such as blocking executable content from email and webmail clients, preventing Office applications from creating child processes, and more.
ASR Rules:
- Block execution of potentially obfuscated scripts
- Block Office communication application from creating child processes
- Block all Office applications from creating child processes
- Block Win32 API calls from Office macros
- Block executable files from running unless they meet a prevalence, age, or trusted list criterion
- Block JavaScript or VBScript from launching downloaded executable content
- Block untrusted and unsigned processes that run from USB
- Block Adobe Reader from creating child processes
- Block credential stealing from the Windows local security authority subsystem
- Block abuse of exploited vulnerable signed drivers (Device)
- Block persistence through WMI event subscription
- Block Office applications from injecting code into other processes
- Use advanced protection against ransomware
- Block executable content from email client and webmail
- Block process creations originating from PSExec and WMI commands
- Block Office applications from creating executable content
- Enable Controlled Folder Access
Step 4: Assign the ASR Policy
Assign the ASR policy to the relevant device groups in your organization.
Step 5: Monitor and Adjust
Regularly monitor the effectiveness of the ASR rules and make adjustments as needed. Intune provides detailed reporting and analytics to help you track the impact of the rules and identify any areas that may require further refinement.
Blocking Windows 11 Vulnerabilities with ASR
Windows 11, like any operating system, has vulnerabilities that malicious actors can exploit. Using ASR rules, you can significantly reduce the risk of exploitation. Here are some specific ASR rules that help block Windows 11 vulnerabilities:
Block executable content from email and webmail clients
This rule prevents executable files from being launched from email attachments or webmail clients. By blocking these files, you can mitigate the risk of malware being delivered through phishing emails.
Prevent Office applications from creating child processes
Office applications are often targeted by attackers who use them to execute malicious code. This ASR rule blocks Office applications from creating child processes, effectively stopping many types of attacks that rely on this technique.
Block credential stealing from LSASS
The Local Security Authority Subsystem Service (LSASS) is a common target for attackers seeking to steal credentials. This ASR rule blocks processes attempting to access LSASS, preventing credential theft and lateral movement within the network.
Block executable files from running unless they meet a prevalence, age, or trusted list criterion
This rule blocks executable files that do not meet certain criteria, such as being widely used, being older than a specified number of days, or being on a trusted list. This helps prevent the execution of potentially harmful files.
Best Practices for Using ASR Rules
To maximize the effectiveness of ASR rules, consider the following best practices:
- Continuously update ASR rules: As new threats emerge, Microsoft regularly updates ASR rules. Ensure that your policies are always up-to-date to protect against the latest threats.
- Test before deployment: Before applying ASR rules to your entire organization, test them on a small group of devices to identify any potential issues or conflicts.
- Educate users: Inform your users about the significance of ASR rules and how they contribute to overall security. Encourage them to report any issues or suspicious activities.
Conclusion
Microsoft Intune’s Attack Surface Reduction rules are a powerful tool for enhancing the security of your Windows 11 devices. By implementing these rules, you can effectively block vulnerabilities and protect your organization from a wide range of threats. Through regular monitoring and updates, you can ensure that your security measures remain robust and adaptive to the evolving threat landscape. Embrace the power of ASR rules and take a proactive approach to safeguarding your digital environment.
